Kickstarting Your Idaptive MFA Integration With Cortex By Palo Alto Networks
We’ll be in booth # 300F at Ignite19. Please come by our booth for a demo of Intelligent MFA for Cortex.

Idaptive’s unique threat intel data ingestion architecture allows us to keep expanding our ecosystem of partners. This rich ecosystem of partners like Palo Alto Networks help us in augmenting the data-set we use to refine and base our adaptive, risk-based Multi-factor Authentication (MFA).
In March, my colleague Lee Godby published a blog announcing our integration with Palo Alto’s Cortex Data Lake (CDL), which helps us in augmenting our analytics with threat intelligence coming from Palo Alto Networks. In this blog, we’ll expand on some of the technical components and flows leveraged to make this integration happen.
First, the elements required in order for this integration to work:
- Pre-requisites
- Registration & Initial Configuration: How Idaptive registers with the Cortex Data Lake
- Data Collection: Once registered, we collect data from the Cortex Data Lake
- Threat Intelligence: Ingest threat intelligence from CDL and attribute appropriate risk score
- Step-Up Adaptive MFA: Adapt access security based on the additional intel from CDL
Pre-requisites
Before you start configuring the integration with PAN, you must meet the following requirements:
- Your company must have a Cloud Services Apps account with PAN. Register for an account at https://apps.paloaltonetworks.com.
- You must have an Idaptive tenant with Analytics entitlement turned on. Please visit our free-trial site to spin up your tenant in minutes.
Registration & Initial Configuration
Idaptive+Palo Alto Networks customers would go to the CDL apps webpage to activate the Idaptive app:
CDL uses OAuth Authorization Code Grant flow to grant an access key to the Idaptive Analytics client during the registration process. Renewal of the token happens behind the scenes and the user does not need to specifically request one. Once the app is activated on the CDL’s apps page, the user would be prompted to login to the Idaptive Analytics Service, which will complete the OAuth authorization grant.

The integration then appears in the Analytics portal under Settings->Integrations.
More details can be found here.
Data Collection
Once the integration between the Idaptive Analytics Service and the Palo Alto Networks’ CDL is established, it is now time to start collecting data from CDL, which can then be used to refine access security of the thousands of resources that Idaptive is protecting.
Idaptive, with its distributed sensor-based collection architecture, is able to collect data associated with various contexts and feed that to its central analytics engine to compute the risk score associated with the various access events.
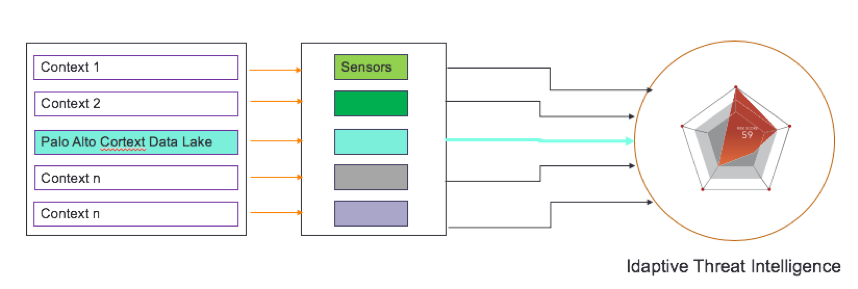
Once the sensor is installed, the user must configure the source (in this case, Palo Alto Networks CDL), setup the collection rules, and then either manually or automatically collect snapshots.
For details on how to install connectors, please check the Idaptive online docs here.
For more details on configuring the sensor for Palo Alto Networks CDL as the source, please see the docs here.
Threat Intelligence
This is the last and most important part. The data collected from CDL is mapped to a risk model on Idaptive, resulting in risk scores. The risk scores are then used to determine access rules to the resources being protected.
The below figure tries to capture the information flow:
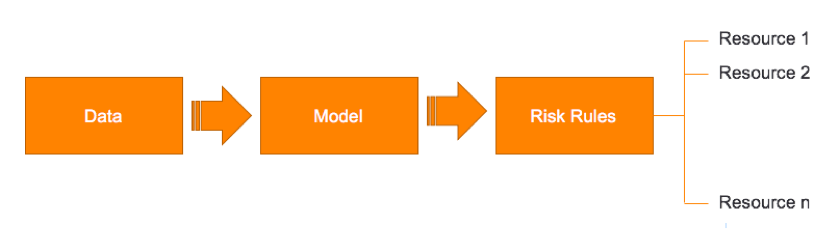
For example, one of the rules could be to assign a high-risk score for all users found in the Palo Alto Networks threat list.
More details on how to associate the data collected from CDL to risk score in Idaptive can be found here.
Step-Up, Adaptive MFA
Should an alert event occur, Idaptive Analytics Service allows the user to easily step up authentication factors for a given application’s access. This can be done by setting up a per-app access policy based on “risk” as the context.
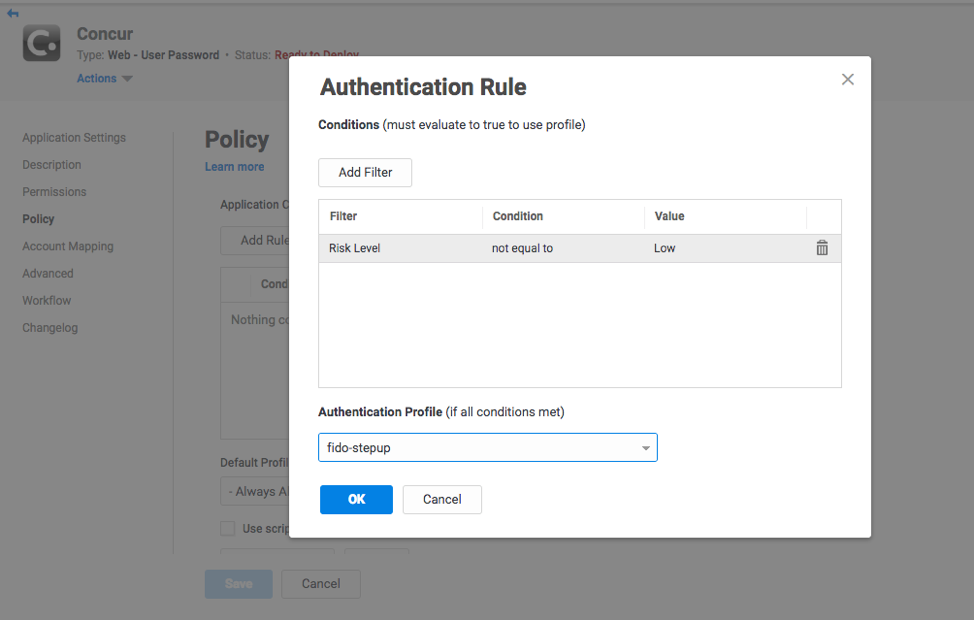
Instead of relying on hardcoded rules, Idaptive Analytics Service produces a risk score for any access attempt (for example, login, device OS, application usage, etc.) by leveraging machine learning. The risk-based access policies can be set up to stop anomalous activity in real time – at the point of access.
Since access control decisions are made based on risk level, Idaptive Analytics Service can be easily created to:
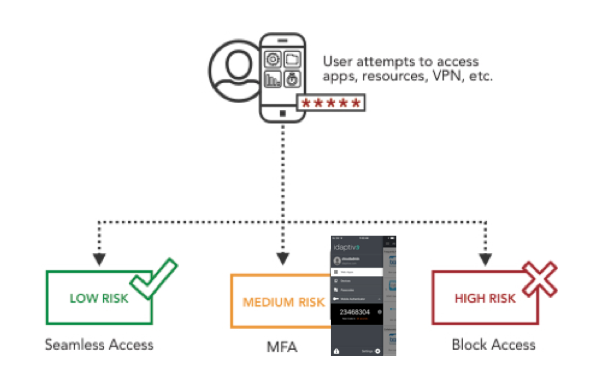
- Ease low-risk access for typical app access requests
- Prompt MFA when requests are outside of typical user behavior
- Block access entirely for requests that present high risk
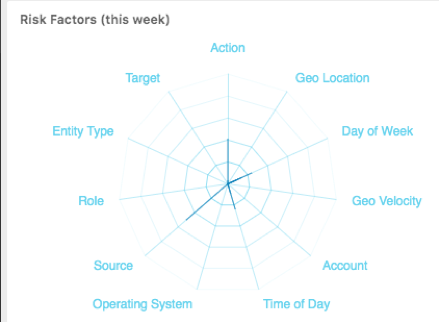
You can also check for the various factors impacting the risk scores in a given timeframe.
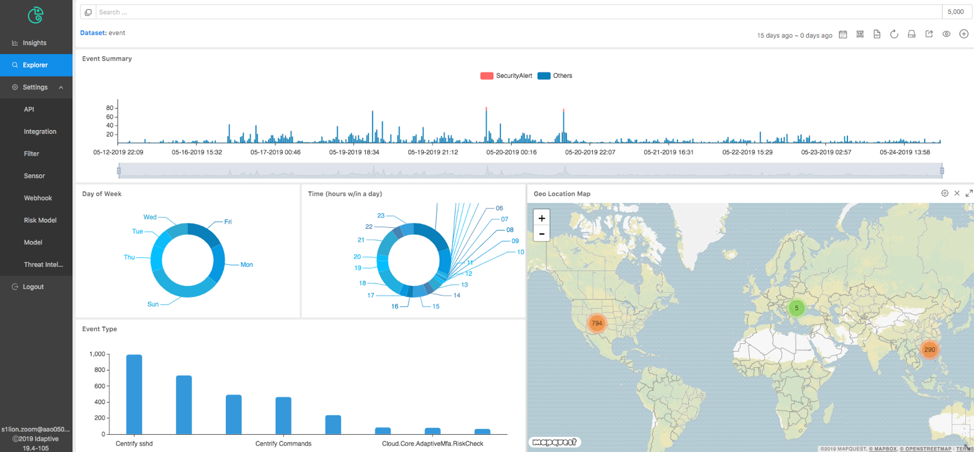
Last but not least, Idaptive’s Analytics Portal offers a rich dashboard to drill down into security events and get more information about the event or the resources impacted by it.
In summary, the integration between Palo Alto Networks’ CDL and Idaptive Identity Services offers our joint customers a unique solution which leverages network security context to make real-time, risk-based access decisions, and adapt and react to security breaches that jeopardize critical applications and resources.
For more details, visit the analytics product and documentation sites.


