Adaptive MFA Using Analytics and Artificial Intelligence

As risk-aware security products powered by machine learning, artificial intelligence and big data technologies emerge and evolve, they will rightfully become part of the standard arsenal for enterprises in the fight against security breaches. In the context of Identity and Access Management, AI can provide security answers traditional solutions cannot. This starts with understanding risk through real-time analytics such as Idaptive Analytics Service.
THE EVOLUTION OF IAM
In recent research notes published by leading analysts on how the modern identity and systems to protect are evolving, great emphasis is being laid on the following characteristics of modern Identity and Access Management (IAM) systems:
- That the modern IAM system will primarily be delivered as a service in the cloud (IDaaS)
- How it will leverage a centralized risk-based, adaptive access engine to counter the ever-increasing sophistication in cyber attacks
- That the quality of the adaptive access engine will be driven by how efficiently the centralized, machine-learning based, analytics engine is able to consume contexts from various network, device and identity analytics sources.
Some other interesting data published by leading analysts:
According to analysts, companies will spend up to $96 billion worldwide on security this year. Research by Centrify (Idaptive’s parent company) and Dow Jones suggests that up to 79% of companies have experienced a significant breach.
Forrester estimates that 80% of security breaches involve credentials. This underscores the importance of intelligently invoking more stringent authentication policies when required, thus ensuring that user experience does not have to be compromised in the pursuit of a robust and resilient identity management and access security solution.
Traditional Identity and Access Management (IAM) products have been trying to resolve the problem by leveraging static rules to secure access to business-critical applications and identity and account provisioning in those target applications, which creates numerous blind spots and challenges e.g. improper policy setup, poor user experience etc.
AI AND MACHINE LEARNING TO THE RESCUE
Designed to learn and adapt, artificial intelligence systems are capable of perceiving minuscule moves in online undercurrents. AI is much more capable than humans in identifying blind spots, protecting identities and business critical applications, detecting cyber threat, and responding to the ongoing threat and providing the recovery solution.
AI is the answer to the traditional rule- and policy-based control type of security that is no longer effective, especially in the context of IAM. AI can secure the enterprises networks against the unknown, as opposed to the traditional solutions that can only protect against the known.
Idaptive Analytics Service (IAS), a multi-tenant cloud service, is applying AI and big data analytics to offer intelligent, real-time access security so that improper security policy, unnecessary permission, and access anomaly can be eliminated or detected for monitoring with User Entity Behavior Analytics. It creates a baseline to understand a user or entity’s behavior on a regular basis.
Administrators can explore this data to understand how the privileged account is being used via various tools that IAS provides. Meanwhile, IAS automatically assesses risk based on a constantly-evolving user, endpoint and application behavior patterns. Once the user and/or entity behavior begins to deviate from its normal behavior, IAS then assigns a risk score, enforces an appropriate access decision, and adaptively collects additional data using advanced real-time machine learning algorithms.
NEW PUBLIC SECTOR REQUIREMENTS
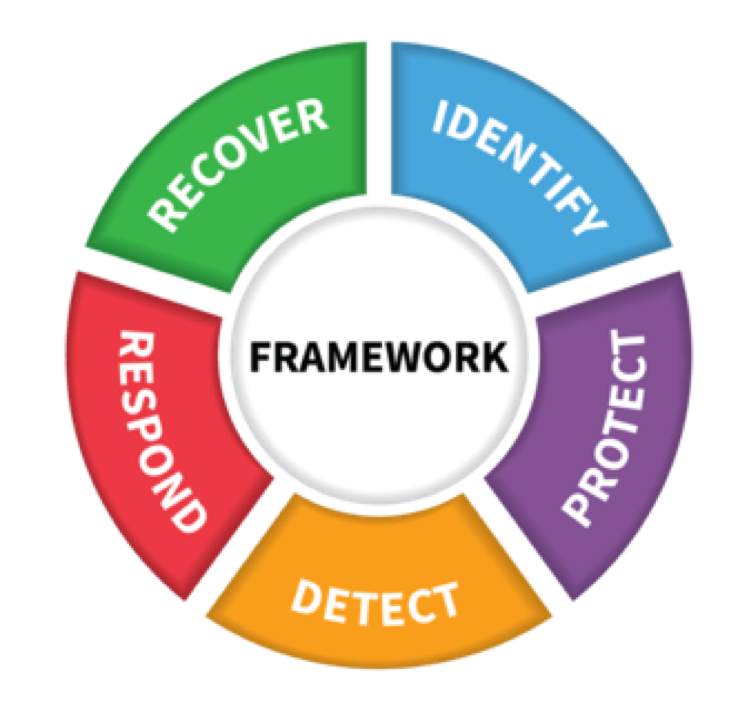
The NIST Cybersecurity Framework (CSF) is U.S. Government guidance for private sector organizations that own, operate, or supply critical infrastructure. It establishes basic processes and essential controls for cybersecurity.
CSF consists of five concurrent and continuous Core Functions: Identify, Protect, Detect, Respond and Recover. On May 11, 2017, the presidential executive order on strengthening cybersecurity of federal networks and critical infrastructure was issued and explicitly mandates that federal agencies should implement the Cybersecurity Framework (CSF). According to Gartner, by 2020, more than 50% of organizations will use the NIST Cybersecurity Framework, up from the current 30% in 2015.
IDENTIFY, PROTECT, DETECT, RESPOND & RECOVER
Idaptive Analytics Service uses the five core functions of CSF as key reference points and provides a strategic view of the lifecycle of an organization’s cybersecurity risk management. The service can also help organizations to address most of the CSF controls and metrics related to identity access management. The near real-time insights and controls, which are provided to IT security professionals, auditors and executives, can be categorized into the following:
1. Identify
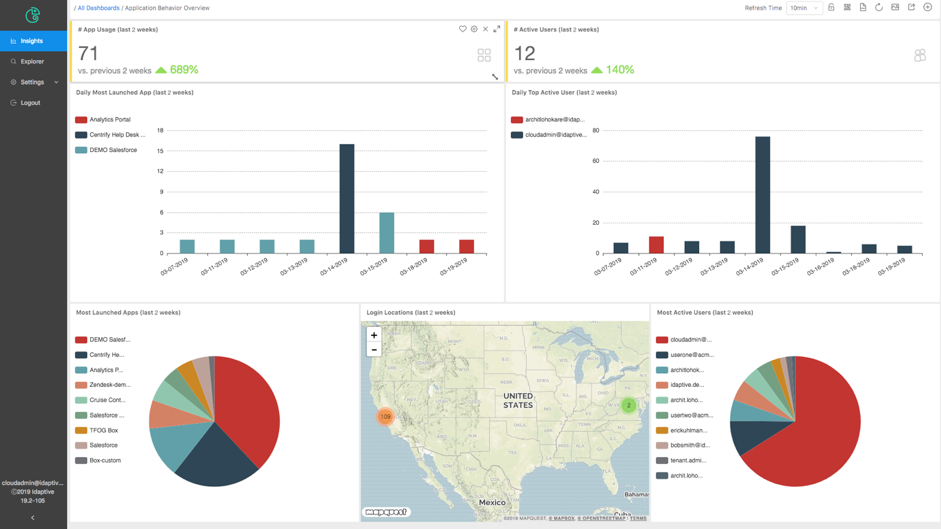
Idaptive Analytics Service collects not only the time series event of all access and activity of all users but also the versioned access entitlement models (also referred to as “authorizations,” “privileges,” “access rights,” “permissions,” “rules,” and/or “policies”). By cross-referencing time series event data and model data such as access entitlements, IAS can be used to identify full contextual function areas such as asset management and risk management. For example:
- Built-in dashboards provide 360-degree view of identity and access with details one click away.
- Discover the identity and access risks, e.g. user role membership and associated apps and devices.
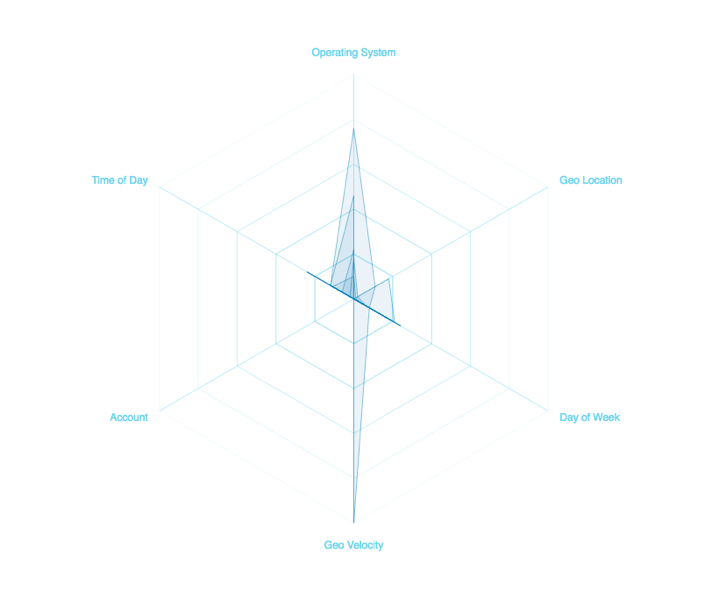
- Discover user behavior patterns w.r.t:
- Geo Location
- Geo Velocity
- Day of Week
- Time of Day
- Device OS
2. Protect
Instead of relying on hardcoded rules, Idaptive Analytics Service produces risk score for any access attempts (e.g. login, Device OS, application usage etc.) by leveraging machine learning. The risk-based access policies can be setup to stop anomalous activity in real time – at the point of access.
Since access control decisions are made based on risk level, Idaptive Analytics Service can be easily created to:
- Ease low-risk access for typical app access requests
- Prompt MFA when requests are outside of typical user behavior
- Block access entirely for requests that present high risk
3. Detect
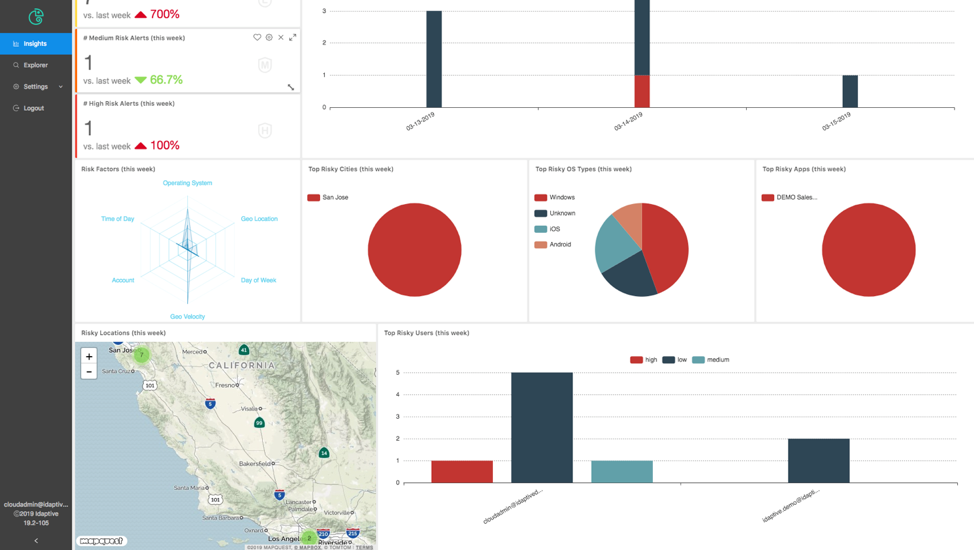
Idaptive Analytics Service continually monitors the near real-time event stream and detects the anomalous behavior and potential threats with a threat detection engine. This engine uses big data analytics and real-time machine learning algorithms to automatically identify the risks from the massive amount of access event data and access entitlements data.
Once a threat is detected, it annotates the risky event with risk score as well as the risk distribution and create an alert. Meanwhile, IAS learns and updates the user/entity behavior profile based on the real-time event stream that it scans through.
IAS-enabled security teams to see the system access, anomaly detection in high resolutions with analytics tools such dashboards, explorer views, and investigation tools.
To illustrate a typical threat monitoring and investigation flow:
- Administrator starts with “Exploring events” from the explorer tab
- Drills down into a risky event and focus into it in the explorer view and review the risk and risk distribution
- Checks for any breaches
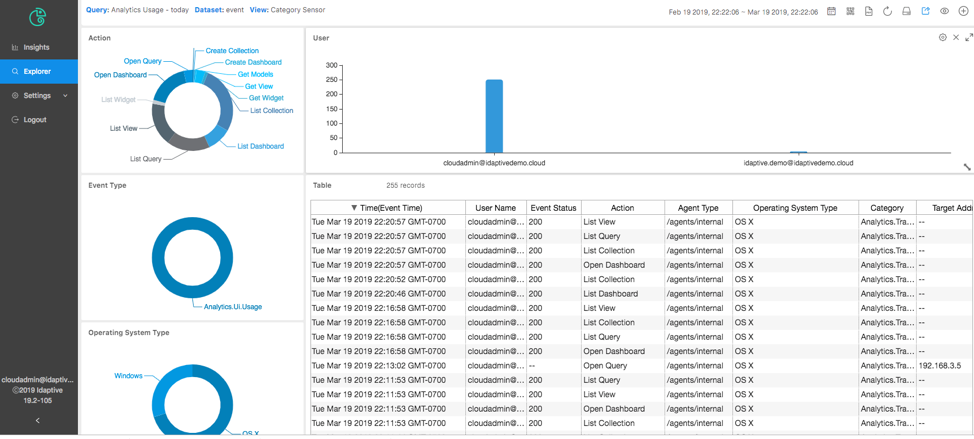
Real-time Threat Monitoring and Investigation
4. Respond
Idaptive can evaluate and combine a large number of conditions to determine access to a given application including time of day (e.g. work hours), inside/outside corporate network, previously authenticated with a high auth policy, membership in a specific role(s), attribute(s)/group(s) of the user, attribute(s) of a device (device type, enrolled/not enrolled, managed/not managed other attribute(s) of the device), location/country of origin of the auth request (based on IP), IWA/Kerberos used, thick client app attributes and callouts to external web services (REST APIs) including external risk-engines as part of evaluation access conditions.
Should an alert event occur, Idaptive Analytics Service allows the user to easily step up authentication factors for a given app access.
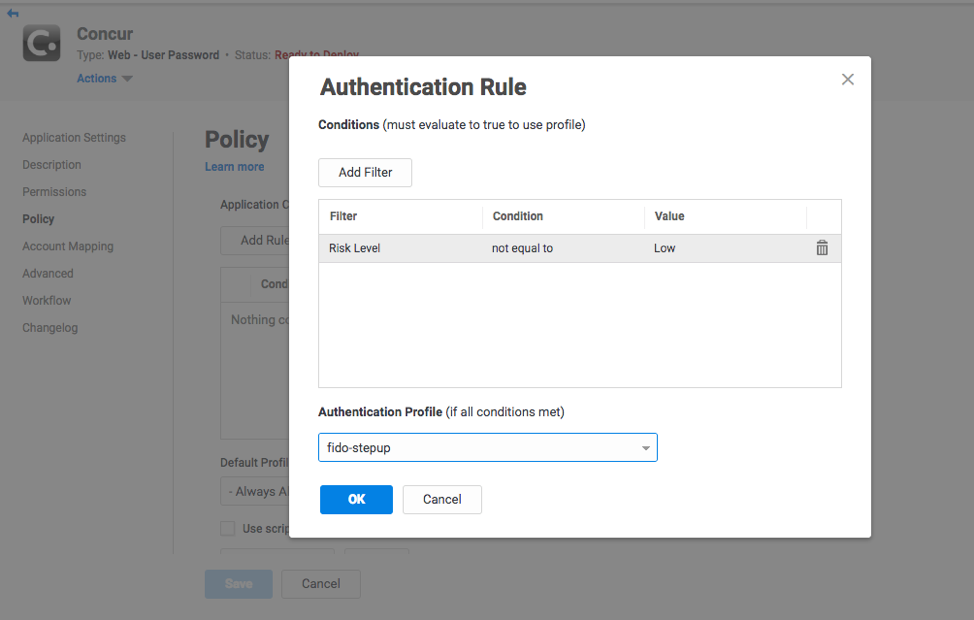
5. Recover
Idaptive Analytics Service continuously monitors and learns from the data it collects from various data sources. Based on the historical data, IAS provides quick ways to limit the exposed attack surface by offering access controls based on roles memberships and fine grain application level entitlements control based on the least privilege model.
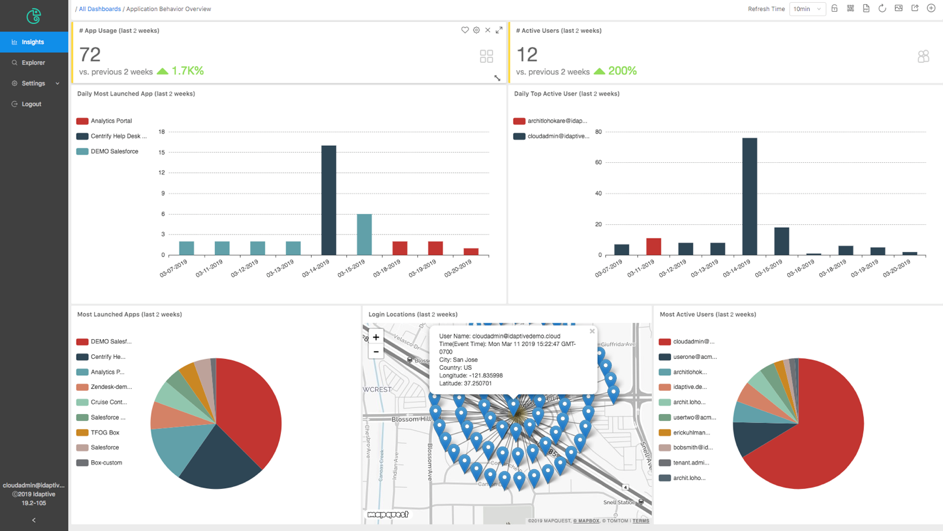
User & App Access Policy Management
- Idaptive provides a flexible engine that allows administrators to manage policies for workflows such as provisioning, access certification, etc. by identity, group, application, and other customizable attributes and conditions
- The Idaptive Platform enforces Role-Based Access Control with the ability to assign specific administrative rights to specific Roles. Administrators can create a Role for business users with the administrative right of Report Management, so that these business users can review and certify user accounts as needed.
- Administrators can setup access policies that leverage Risk scores from the Analytics Service to make real-time decisions for access (allow, block or require MFA).
It is pretty obvious that the emergence of risk-aware security products powered by machine learning, artificial intelligence, and big data technologies will quickly become the de facto standard weapon for enterprises to fight against security breaches. That starts with understanding risk through real-time analytics, such as Idaptive Analytics Service.
For more details, visit the analytics product and documentation sites
This is an adaptation of the original article published here.


