Idaptive Release 19.5 Is Now Available
Release 19.5 adds support for real-time security incident notifications, local account linking, global endpoint permissions, and more.

With release 19.5, Idaptive now supports the following features:
Enhanced provisioning for G Suite
You can now provision additional attributes, such as group alias, group owner, and manager as well as secondary email into the Google G Suite Directory. This allows you to correctly map group and user information between Active Directory (source directory) and Google Directory. To learn more about G Suite provisioning, see here.
Enhanced provisioning for Salesforce
You can now provision users and custom attributes into Salesforce using the Salesforce app template in the Idaptive App Catalog. Previously, provisioning users into Salesforce required using the SCIM protocol, which has limited support for custom attributes. Now, you can use the out-of-the-box Salesforce app template to provision users with custom attributes. To learn more about Salesforce provisioning, see here.
Enhanced SCIM provisioning
You can now choose which attributes are passed during SCIM provisioning. This enables you to omit attributes which do not have a set value or which are already provisioned in the target app. Previously, you could not deselect attributes in the SCIM payload, causing some provisioning jobs to fail when an unexpected value was present in one of the attributes. Now, you can explicitly define attributes to be sent in the provisioning script to ensure script executes successfully. To learn more about SCIM provisioning, see here.
Real-time security incident notification via email
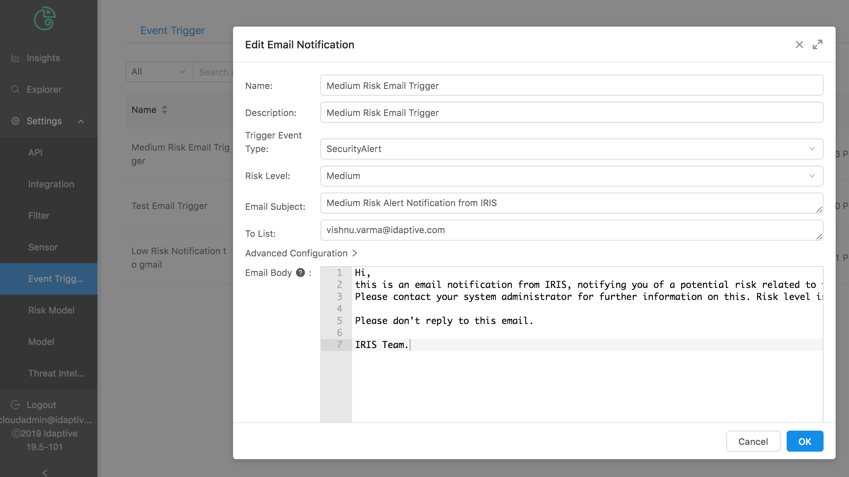
You can now automatically send security incident notifications to pre-defined email aliases. For example, you can notify your security team when a high-risk incident occurs and provide them incident details, including risk level and users involved. Previously, administrators needed to be logged into the Idaptive platform or set-up integrations with third-party tools to be notified of security incidents. Now, administrators can receive email notifications in real-time when security incidents occur. To learn more about security incident notifications, see here.
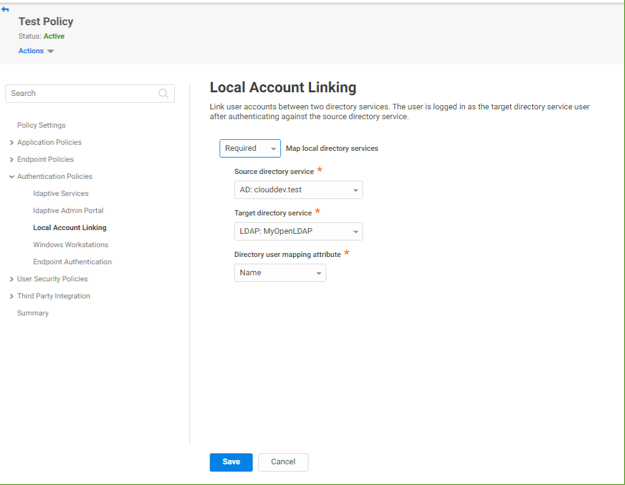
Local account linking
You can now map user accounts between two directories based on a matching attribute. For example, you can link user identity in Active Directory with the one in the LDAP Directory, based on user’s email. This enables you to enforce authentication against a preferred directory when the user is present in multiple directories. You can also utilize this feature when migrating from an environment with multiple directories to standardize on one directory while ensuring that the end-users' login experience remains unchanged. To learn more about local account linking, see here.
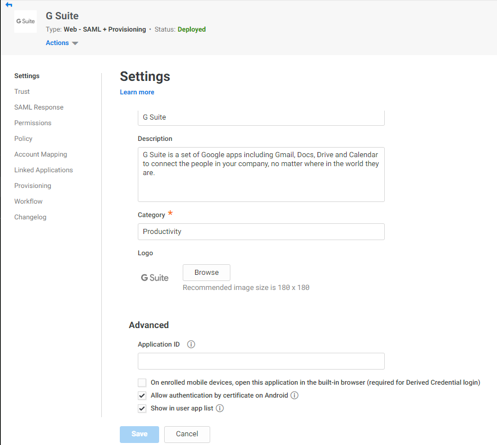
Certificate-based authentication for G Suite
You can now configure single sign-on for the native G Suite app on Android devices. Previously, you could leverage single sign-on to access G Suite apps through the Idaptive App or User Portal. Now, you can use your enterprise credentials to access the native G Suite app using certificate-based authentication. This allows you to access the G Suite app without additional authentication, once your Android devices is secured with Idaptive platform. To learn more about certificate-based authentication for G Suite, see here.
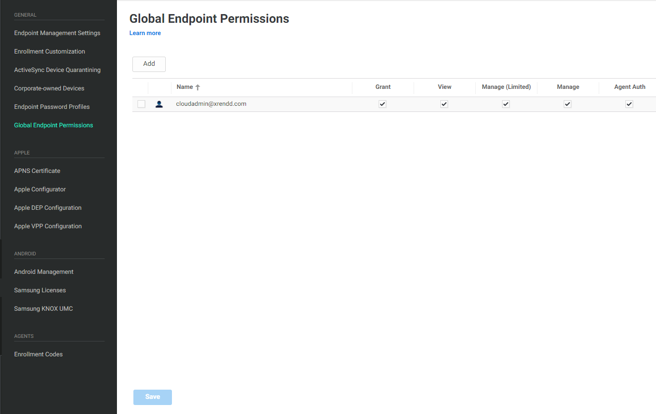
Global endpoint permissions
You can now provide specific groups, roles, or users the ability to access all Mac and Windows endpoints managed by Idaptive. Previously, you had to grant individual users access to specific devices. Now, you can grant global endpoint permissions to appropriate groups, roles, or users to simplify device management. For example, you can use global permissions to grant users in the “IT HelpDesk” role the ability to lock and unlock devices, but not issue other types of device commands. You can use the same capability to provide users with the “Admin” role the ability to log in to all Mac and Windows devices and execute commands such as remote wipe or remote lock. To learn more about global endpoint permissions, see here.
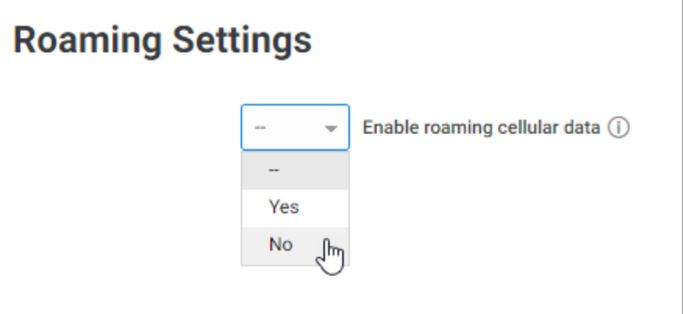
Control data roaming for Android devices
You can now enable or disable data roaming option on enrolled Android devices with a policy setting. Previously, you could not override the end-user preferences for data roaming. Now, you can restrict data roaming through policy. For example, you can create a policy to disable data roaming on managed Android devices and minimize your international data costs. To learn more about creating policies to manage data roaming, see here.
Additional features and improvements in the 19.5 release:
- Idaptive Support Portal app template: Enable single sign-on into the Idaptive Support Portal using the new Support Portal app template
- Directory lookup order: Specify the directory lookup order to enable faster account search.
- Support for Android 10: Enroll Android 10-based devices into Idaptive platform.
- Record serial number for Android O devices: Record serial numbers for devices running Android O after device enrollment.
- Support for additional ZSO authentication attempt: Enable certificate-based authentication attempt when accessing apps and Idaptive portal on Android devices.
For more information on 19.5 release, please visit release notes.


