NIST 800-63-3 Digital Identity Guidelines – A Primer

The National Institute of Standards and Technology (NIST), in June 2017, published a new set of guidelines as part of their special publication 800-63-3 that provided technical requirements for federal agencies implementing digital identity services. These guidelines have been instrumental in helping me and many others in the Identity and Access Management space learn, think through, and build out product strategy for our product lines. I’ve had the privilege and good fortune to speak to many of Idaptive’s customers about these guidelines in the context of their identity and authentication assurance needs, and I’ve always been encouraged and inspired by the immense amount of interest and debate these guidelines generate. Also, I recently had the great privilege to speak to some incredibly smart folks at NIST about Idaptive and our technology, and it made me realize that it was time to put pen to paper and provide a quick perspective on these guidelines. This is part one of a 4-part blog series.
The 800-63-3 Digital Identity guidelines have expanded on a singular concept of level of assurance (LOA) for all electronic authentication of digital identities that was originally introduced in 800-63-2. The new guidelines are more specific to the business needs and use cases where digital identities are to be used. Very broadly, the new guidelines cover three processes, Identity Proofing, Digital Authentication and Federated Identity Management.
The Digital Identity, as NIST explains it
The digital identity is a unique representation of the physical subject, or individual (in Idaptive’s world, given our focus), in the online world, that is engaged in an online transaction. This transaction could be as simple as just logging into a single service, or as complex as performing an e-commerce transaction across multiple services or websites. The purpose of the digital identity is often limited to use in the context of the service alone and does not necessarily need include or need all the physical world attributes or information of the individual.
Identity Proofing, Digital Authentication and Federated Identity Management
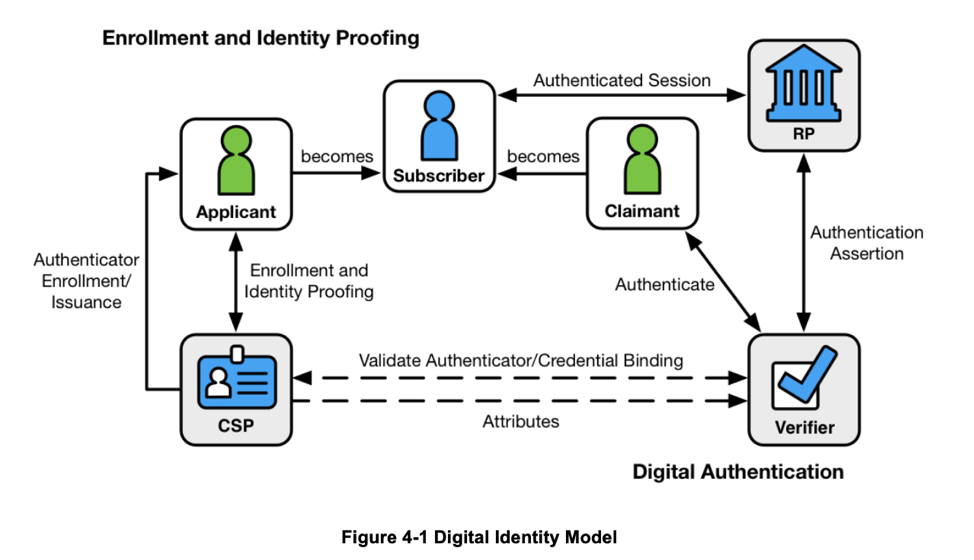
Figure: Digital Identity Model, Source: NIST Special Publication 800-63 Volume 3 Revision 3, Digital Identity Guidelines
The image above provides an excellent overview of the key processes digital identities participate in. CSP, in this diagram, refers to a Credential Service Provider that is responsible for performing the enrollment, identity proofing and issuance processes. The Verifier is responsible the service or the party that verifies the individual’s digital identity.
Enrollment and Identity Proofing is the process of assuring that an individual (or subject) is who they claim to be, and “IAL” (Identity Assurance Level) refers to the level of assurance (or “strength”) with which this assurance can be described. An example of proofing an individual would be to ask them questions about them that only they (hopefully) would know. Alternately, another example would be to ask them to submit a copy of their state issues Driver’s License, proving proof of possession of a state attested identity document.
Digital Authentication is the process of an individual attempting to access a service, and “AAL” (Authentication Assurance Level), similarly, is used to provide assurance that the individual accessing a service is possession of one or more authenticators associated with them. An example of this would be to send a one-time password to the individual’s registered phone via a notification or a text. Another example would be to ask the user to authenticate using their Personal Identity Verification, or PIV card.
Finally, Federated Identity management involves a user, authenticated by a third party Identity Provider (IdP), attempting to access a service (Service Provider) or a Relying Party (RP) via a token or an assertion that the IdP sends to the service, and “FAL” (Federated Assurance Level) refers to the strength of that assertion that is used to communicate authentication and attribute information to the RP. 800-63-3 is further broken down into 800-63-A which provides guidelines on Enrollment and Identity Proofing and covers Identity Assurance Levels, 800-63-B which provides guidelines on Authentication and Lifecycle Management and covers Authentication Assurance Levels and finally, 800-63-C which provides guidelines on Federation and Assertions, and covers Federated Assurance Levels.
Levels of Assurance, at a glance
The NIST guidelines document provides an excellent summary of what constitutes Levels of Assurance for each of the three key processes mentioned above. Levels of Assurance for a process, for all practical purposes, are indicators of the “strength” of the identity and access management controls implemented as part of that process. Typically, they range from level 1 to level 3. Below is a series of tables that are included in the guideline document that provide the summaries.
Identity Assurance Levels

Authentication Assurance Levels

Federated Assurance Levels

Each of these guidelines, by themselves, deserve a series of blogs, if not a whitepaper. To that end my next series of blogs on this topic will focus on providing additional color on 800-63-A, 800-63-B and 800-63-C, how organizations should go about adopting these guidelines and choosing what level of assurance they should ideally target, and how Idaptive can help with achieving high levels of assurance for 800-63-B and 800-63-C. Stay tuned!


