Idaptive Release 20.3 Is Now Available
Release 20.3, scheduled for August 22, 2020, adds support for Single Sign-On to CyberArk Privileged Access Management solutions, enhancements to policy scripting, as well as various UI and operational improvements.

With release 20.3, Idaptive supports the following features:
Single Sign-On
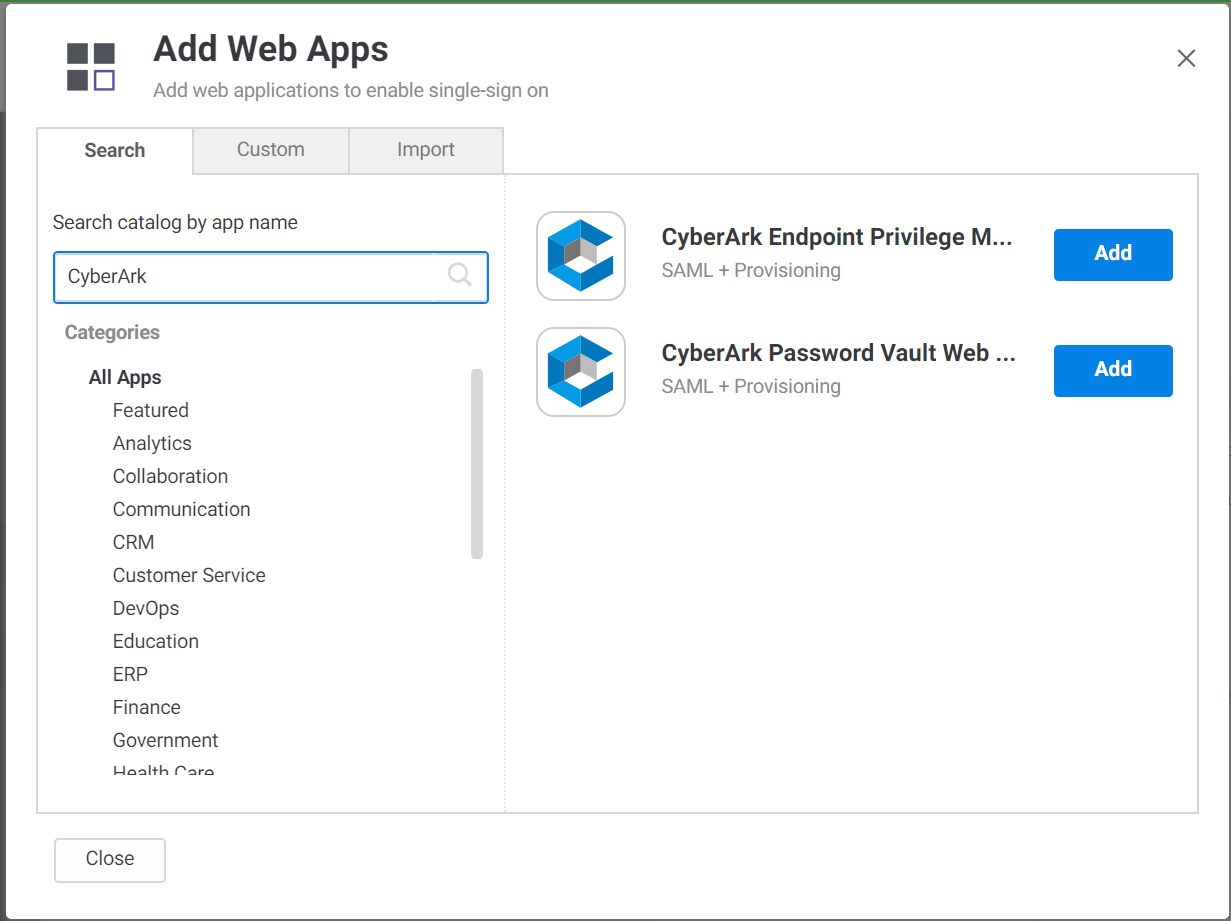
SSO to CyberArk Password Vault Web Access and Endpoint Privilege Manager
You can now easily integrate CyberArk Password Vault Web Access (PVWA) interface and CyberArk Endpoint Privilege Manager (EPM) with the Idaptive Single Sign-On service. This enables you to implement adaptive, risk-based access controls to both PVWA and EPM solutions. PVWA is a fully featured web interface that provides a single console for requesting, accessing and managing privileged credentials throughout the enterprise by both end users and administrators. The CyberArk EPM allows organizations to block and contain attacks at the endpoint, reducing the risk of information being stolen or encrypted and held for ransom. To set up SSO to these CyberArk services, find the respective SAML templates in the Idaptive App Catalog, and follow the steps in the integration wizard.
Multi-Factor Authentication
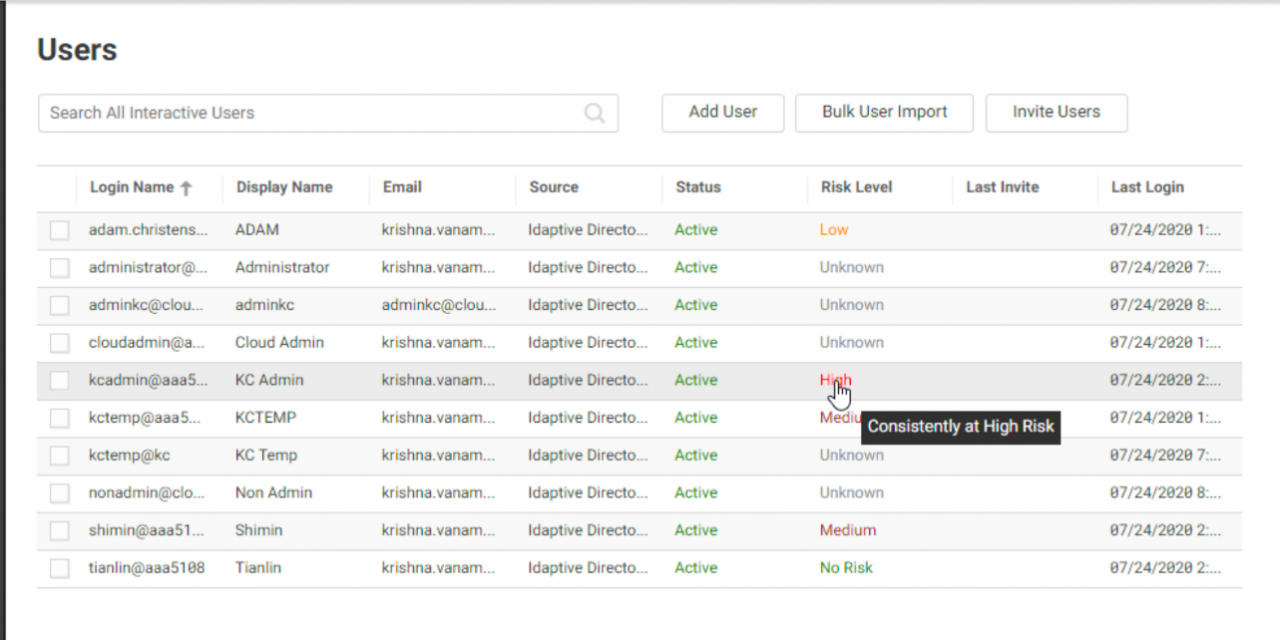
Discover users risk level information directly in the Admin Portal
You can now view risk level information for your users directly in the User section of the Idaptive Admin Portal interface. The risk level calculation leverages machine learning to autonomously analyze each user's activity to determine typical behavior for that user and then continuously compute risk scores that signal the extent of anomalous behavior displayed by that user. With this feature, you can quickly identify high-risk users in your organization and take proactive steps to investigate the root cause of unusual behavior. This feature is currently in beta and will be available to Adaptive MFA customers in future releases.
Policy scripting enhancements
You can use JavaScript to flexibly control the conditions under which users can access an application or when to require additional authentication steps. With this release, you can now use scripting to define risk-based application launch policies, create access rules based on the presence of the Identity Cookie, and specify authentication profiles for an application.
-
Define risk-based application launch policies: You can now use scripting to define conditional access policies that control the ability of users with elevated risk levels to launch specific applications. Previously, you could define risk-based access policies using the graphical interface in the Admin Portal. Now, you can accomplish this task programmatically as well. For example, you can now create an application policy script that prevents users with "high" risk scores from launching applications with customer data. You can also define a policy script to require users with a "medium" risk level to pass secondary authentication prior to accessing specific applications. Users that do not meet the risk-level criteria set in the script will see the application icons grayed out in their User Portal.
-
Check for Identity Cookie presence: The Identity Cookie is added to a user's browser after the user has successfully logged in to the Idaptive Admin Portal or User Portal. With this release, you can now use the presence of the Identity Cookie as part of your conditional access policy script. For example, you can now create an access policy script to allow a more lenient authentication policy if the Identity Cookie is present and require secondary authentication if the no cookie is detected.
-
Specify authentication profile: You can now set the authentication profile for an application using a script. Authentication profiles are used to define the required authentication mechanisms such as passwords, email confirmation codes, mobile authenticators, etc. Previously, you could set the application authentication profile in the Admin Portal interface. With this release, you can also specify the authentication profile in the application policy script.
Lifecycle Management
Enhanced provisioning for NetSuite
You can now leverage additional attributes, such as Department, Location, Status, Hire Date, and Termination Date for automatic user provisioning to NetSuite. This allows you to correctly map user information between a source directory, such as Active Directory or Idaptive Directory and NetSuite.
In addition, with this release, we have updated the NetSuite provisioning integration method to use OAuth 2.0 tokens instead of service accounts.
Additional features and improvements in the 20.3 release
- The option to use Idaptive as a second authentication factor: You now have the option to integrate the Idaptive RADIUS server with your primary authentication solution to provide only secondary authentication by Idaptive.
- Authentication profile preview: You can now preview authentication profile details in the policy settings itself, without having to go to the authentication profile settings of the product. This ensures that you select the appropriate authentication profile for a given policy set.
- Option to enable diagnostic logs for Idaptive Browser Extension (IBE): Diagnostic logs are used for troubleshooting IBE performance. With this feature, end-users can enable diagnostic logging directly in the IBE interface and control the logging level.


