Idaptive Release 20.1 is now available
Release 20.1 adds support for enforcement of MFA factor configurations for new users, an automatic lockout of user accounts associated with high-risk security alerts, and additional triggers for response automation.

With release 20.1, Idaptive now supports the following features:
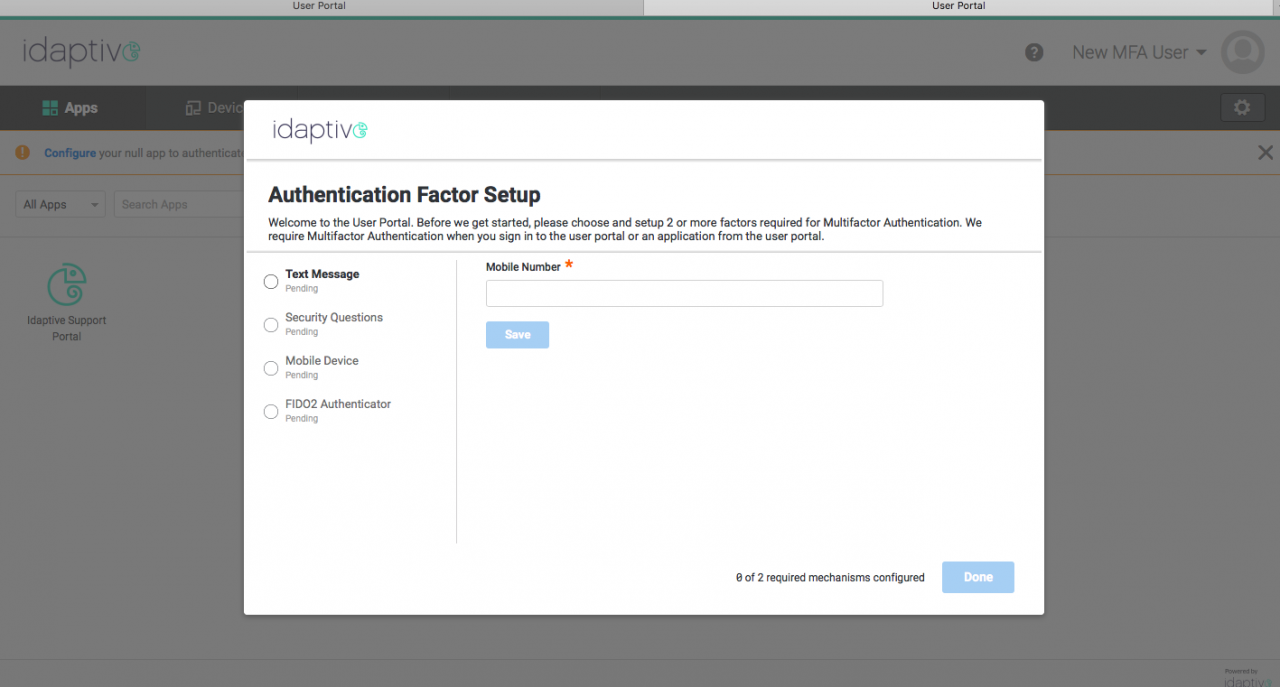
Flexible MFA factor configuration for new users
You can now specify the minimum number of MFA factors that users need to set up before they can proceed to the User Portal. For example, if you have enabled four MFA factors, you can now require users to set up at least two of them during the initial login.
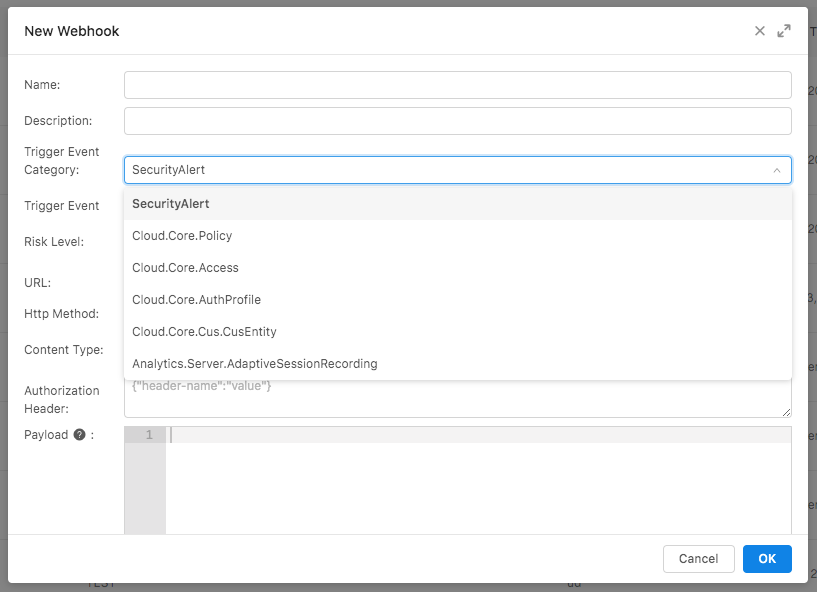
Webhook to limit access for high-risk users
Webhooks allow you to take automatic actions, such as invoking 3rd party web services when a trigger event occurs. With this release, you can now leverage webhooks to lock user accounts associated with high-risk security alerts automatically. For example, a user account can be automatically locked when an access attempt from a blocked IP range is detected. In addition, you can send an email alert to your security team to inform them of the action taken.
Additional triggers for response automation
You can now leverage new trigger events such as user login, user provisioning, rights updates, password changes, and role changes when configuring Response Automation. For example, you can now send an automated alert to your security team when a user’s access rights are updated.
Support for enforcing EMM policies on Android Enterprise devices
We now support the option to enforce Idaptive MDM policies on enrolled Android Enterprise devices.
For more information on the 20.1 release, please see the release notes.


