Idaptive Release 19.6 is Now Available
Release 19.6 adds support for the new Windows and Mac Cloud Agents, passwordless authentication with FIDO2, second factor for certificate-based authentication, mapping of HR attributes to AD attributes, and more.

With release 19.6, Idaptive now supports the following features:
Idaptive Windows Cloud Agent
The new Idaptive Windows Cloud Agent is a lightweight agent that makes it easy for you to join Windows 10 endpoints to the Idaptive Next-Gen Access platform. With Windows Cloud Agent, you can enable end-users to log in to their workstations without direct connectivity to user directories, protect login with adaptive MFA, and enforce device-level security policies. In addition, Windows Cloud Agent provides end-users a convenient self-service capability to unlock their accounts, reset their passwords, or set up offline one-time passcodes for secondary authentication.
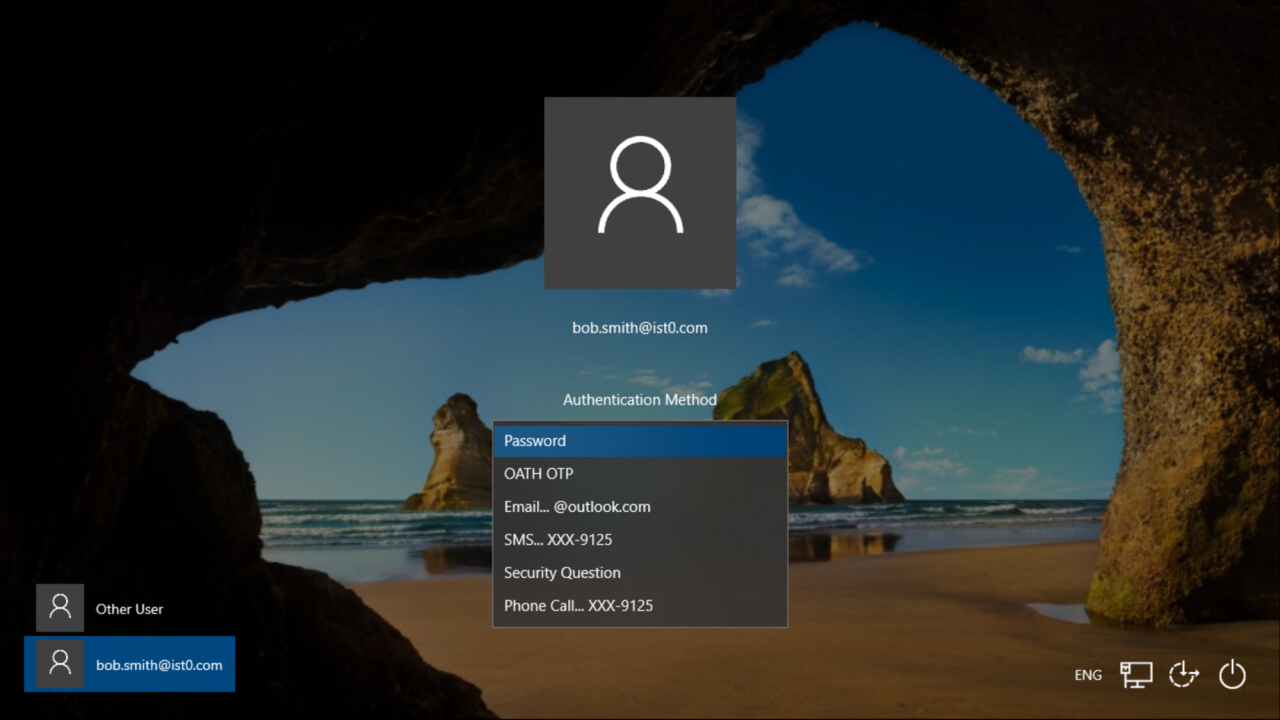
Idaptive Mac Cloud Agent
The new Idaptive Mac Cloud Agent is a lightweight agent that enables you to join Mac endpoints to the Idaptive Next-Gen Access platform. With Mac Cloud Agent, you can enable end-users to log in to their Mac OS X devices without direct connectivity to user directories, protect login with adaptive MFA, and enforce granular device management policies. Mac Cloud Agent also supports certificate-based authentication, which eliminates the need to enter a username and password combination to simplify access to protected resources.
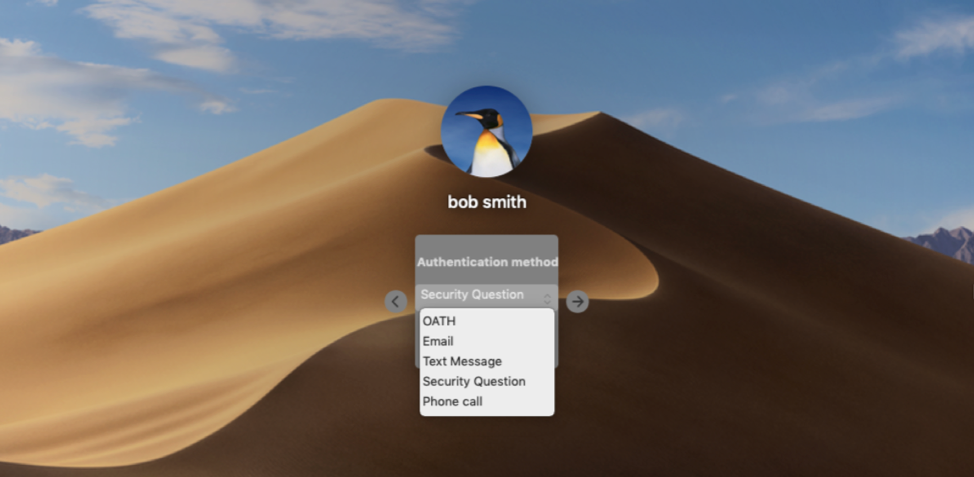
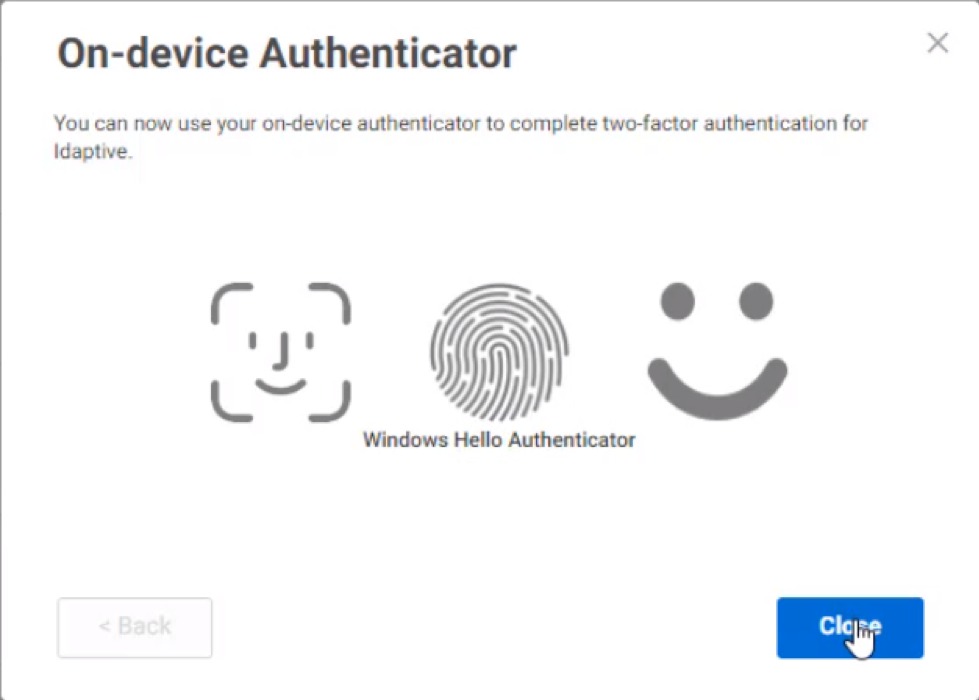
FIDO2 WebAuthN support
You can now use Fast Identity Online (FIDO2) authenticators to secure and simplify access to Idaptive User and Admin Portals on Firefox, Microsoft Edge, Google Chrome, and Apple Safari browsers. FIDO2 WebAuthN standards enable users to authenticate to online services using on-device authentication mechanisms, such as Windows Hello, Mac OS TouchID, Yubico YubiKeys. For example, with FIDO2 support enabled, you can authenticate to the Idaptive Portal without a password by using a fingerprint reader built-in to your laptop.
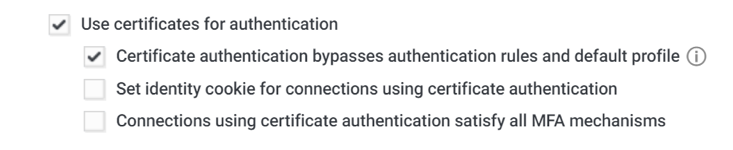
Second factor for certificate-based authentication
You can now require users to pass secondary authentication challenges when they access applications from devices provisioned with digital certificates. You can also define conditional access policies for certificate-based authentication (CBA). CBA allows you to authenticate into applications using a device certificate in place of entering credentials. Previously, conditional access policies did not extend to certificate-based connections. Now, you can create access policies based on the presence of digital certificates on end-user devices. For example, you can configure a policy to require a single authentication challenge for devices with a valid certificate and multiple challenges for devices without certificates, accessing applications from a new location, or missing an identity cookie.
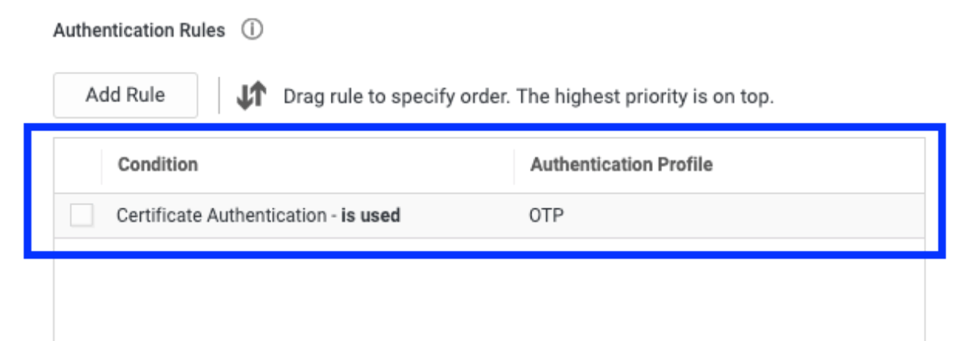
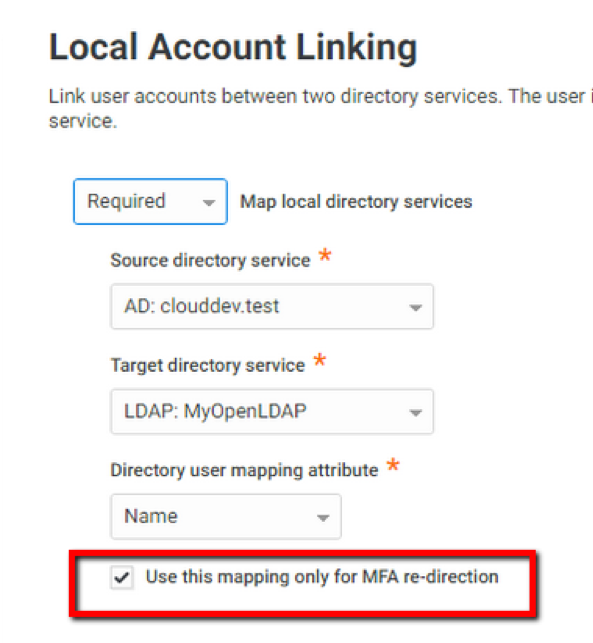
MFA challenges for linked user accounts
You can now enforce a uniform multi-factor authentication policy across all accounts (Active Directory, Idaptive Cloud Directory, or Federated Directory) linked to a single user. Previously, users with multiple accounts had to pass authentication challenges assigned to the specific account they used to access applications or the Idaptive Portal. Now, users will see a consistent set of MFA challenges regardless of the account used to log in. For example, once the user’s accounts in Active Directory and LDAP directory are linked, the user will be able to see secondary authentication challenges previously assigned to the LDAP account even if the user logs in with the Active Directory credentials. This feature is beneficial to organizations with multiple user directories and ensures consistent and secure login experience across all user accounts.
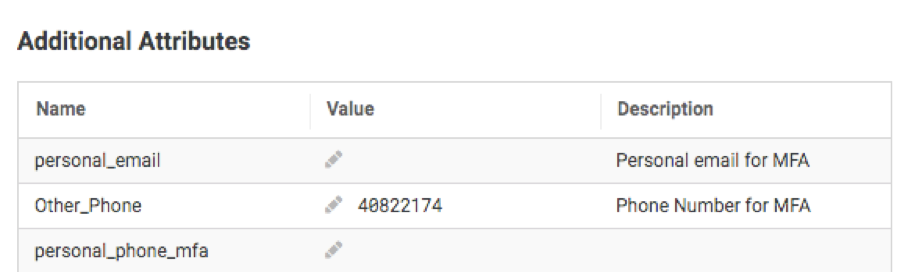
Self-service update of custom user attributes
You can now enable end-users to update custom attributes associated with their directory profile directly in the Idaptive User Portal interface, without involvement from administrators. This helps you to reduce your IT Help Desk costs and improve end-user productivity. Custom attributes, such as secondary phone numbers or personal emails, can be used as additional multi-factor authentication factors. Previously, only administrators could modify custom attribute values. Now, end-users can update these attributes directly in the User Portal and use them for secondary authentication without requiring administrative support. For example, you can create a secondary_phone attribute to capture end-users’ personal email cell phone numbers, which can be used as backup authentication factors. Since these numbers can change over time, this feature now enables end-users to keep their profiles up-to-date without creating IT help desk tickets.
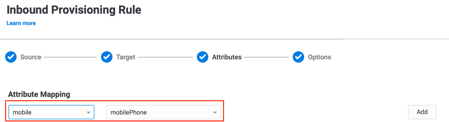
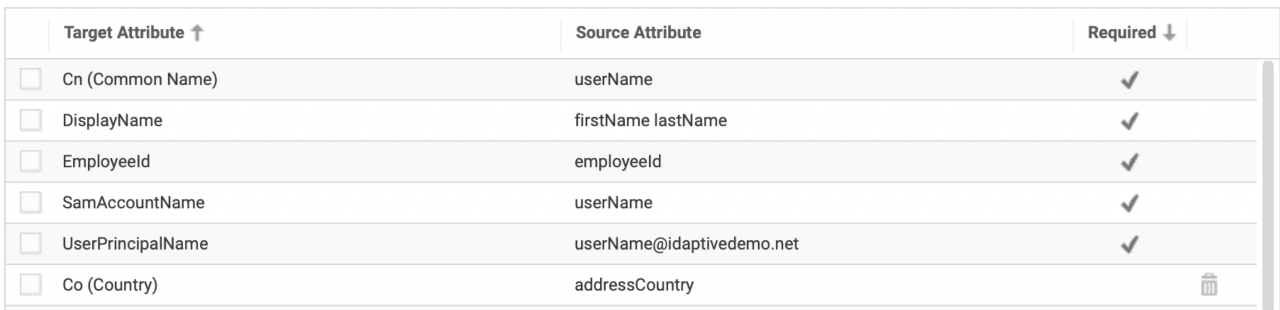
Custom mapping of HR attributes to AD attributes
You can now map any attribute from HR systems, such as Workday, SAP SuccessFactors, Ultimate Software UltiPro, and BambooHR to any attribute in Active Directory to simplify inbound provisioning. Previously, you could only map HR attributes to a fixed number of pre-configured AD attributes. Now, you can use the attribute mapping UI or scripts to map any HR attribute to any Active Directory attribute, including custom attributes. For example, if you want to map the ‘workPhone’ attribute in your HR system to the ‘TelephoneNumber’ attribute in Active Directory, you can add this mapping in the ‘Attribute Mapping’ UI when configuring Inbound Provisioning rules. This feature enables greater automation for the employee lifecycle management and makes it easier to ensure that HR remains the single source of truth for all employee information.
Additional features and improvements in the 19.6 release:
- Session termination: As an application developer, you can now programmatically terminate browser sessions when users log out of applications federated using the OpenID Connect protocol, in addition to revoking app access tokens. Upon session termination, users can be redirected to a pre-determined URL for a better logout experience.
- MFA challenge setup report: You can now simplify your compliance audits with a report that identifies users who have not completed the setup of the required multi-factor authentication challenges.
- Certificate-based authentication for native iOS mail client: You can now seamlessly access work email using the native mail application on iOS devices verified with digital certificates.
For more information on the 19.6 release, please see release notes.


